Digital Trails: Understanding Where Your Data Goes
Every one of us leaves traces – digital traces – in our digitally connected world.
The digital footprint, a collection of all the traces we leave online, is often underestimated, but its importance is immense. Whether you are a board member, a VIP, a politician, or a private individual with a heightened need for protection, everyone is affected. Personal information, whether in business emails, social networking posts, or online transactions, creates a digital profile that presents both opportunities and risks. Despite privacy protections, this information is stored in a database and can be purchased by interested parties.
For executives and public figures, a careless digital footprint can lead to serious security concerns. Cyber-attacks, identity theft or reputational damage are just some of the dangers that can result from unprotected digital data. It is critical to be aware of your online presence and understand how and where personal information can end up online.
In this blog post, we look for clues to help you understand, monitor, and protect your digital footprint. Our goal is not only to provide you with valuable insights, but also to show you practical solutions to strengthen your digital security. Rely on corma’s expertise to protect your digital identity and safeguard your privacy in the digital age.
Executive Summary
Read our in-depth blog post to learn how to protect your personal information online, especially in an age where apps and smartphones are ubiquitous. We look at how digital trails are created as you browse the web, and how you can effectively monitor and secure them.
- Protect your digital footprint while surfing: We highlight how digital trails are created as you browse the web with smartphones and apps, and how you can use tools to monitor and protect them.
- Examine your data with tools: Learn about tools such as the Hasso Plattner Institute’s HPI Identity Leak Checker to check if your data has been compromised.
- Risks of digital footprints: Discussion about the risks of leaving personal data online, especially for people in Potsdam and other cities.
- Sources of personal data: Insight into the various sources of personal data, including lists and databases that are often obfuscated.
- Search engine risks: Discussion of the risks of clicking on search engines and how personal information is made easily accessible.
- Removing old data: Tips for deleting old and unwanted data to block and control your digital footprint.
- Data breaches and information thieves: Discusses the dangers of data leaks and how to investigate and protect your data.
- Data brokers and their role: Analysis of the role of data brokers based on their own statements and how they collect and sell personal information.
- Private data in public registries: Discussion of the availability of private data in public registries and the risks involved.
- Social Media and Online Platforms: Analysis of the role of social media in the dissemination of personal data and the risks involved.
- Digital traces in images: Examining the proliferation of personal photographs on the Internet and its impact on privacy.
- Other online sources: Highlighting other sources where personal data can be found online, including information from the German Federal Office for Information Security (BSI).
- Be aware of your digital footprint: Recommendations for being aware of personal information online and how to protect your digital identity.
Quick Check of Your Digital Identity – Tools and Services to Verify Your Data
To help ensure that your private information is not compromised by data leaks on the Internet, there are useful tools and services you can use. Here are a few recommended options:
- HPI Identity Leak Checker: A service from the Hasso Plattner Institute that allows you to check whether your data has been exposed in known data leaks. A first step in protecting your online accounts from hackers, including notification of leaks!
- Have I Been Pwned?: A widely used platform that helps you determine if your email address or phone number has been compromised in a data breach. Registration with this service is highly recommended!
- DeHashed: A comprehensive marketplace that allows you to search for your personal information in various data leaks. (fee required)
These tools provide a quick and easy way to check and improve your digital security. In addition to the HPI Identity Leak Checker and Have I Been Pwned, there are also special settings in your Google Account that allow you to view and manage your stored information.
The Digital Footprint: An Inventory
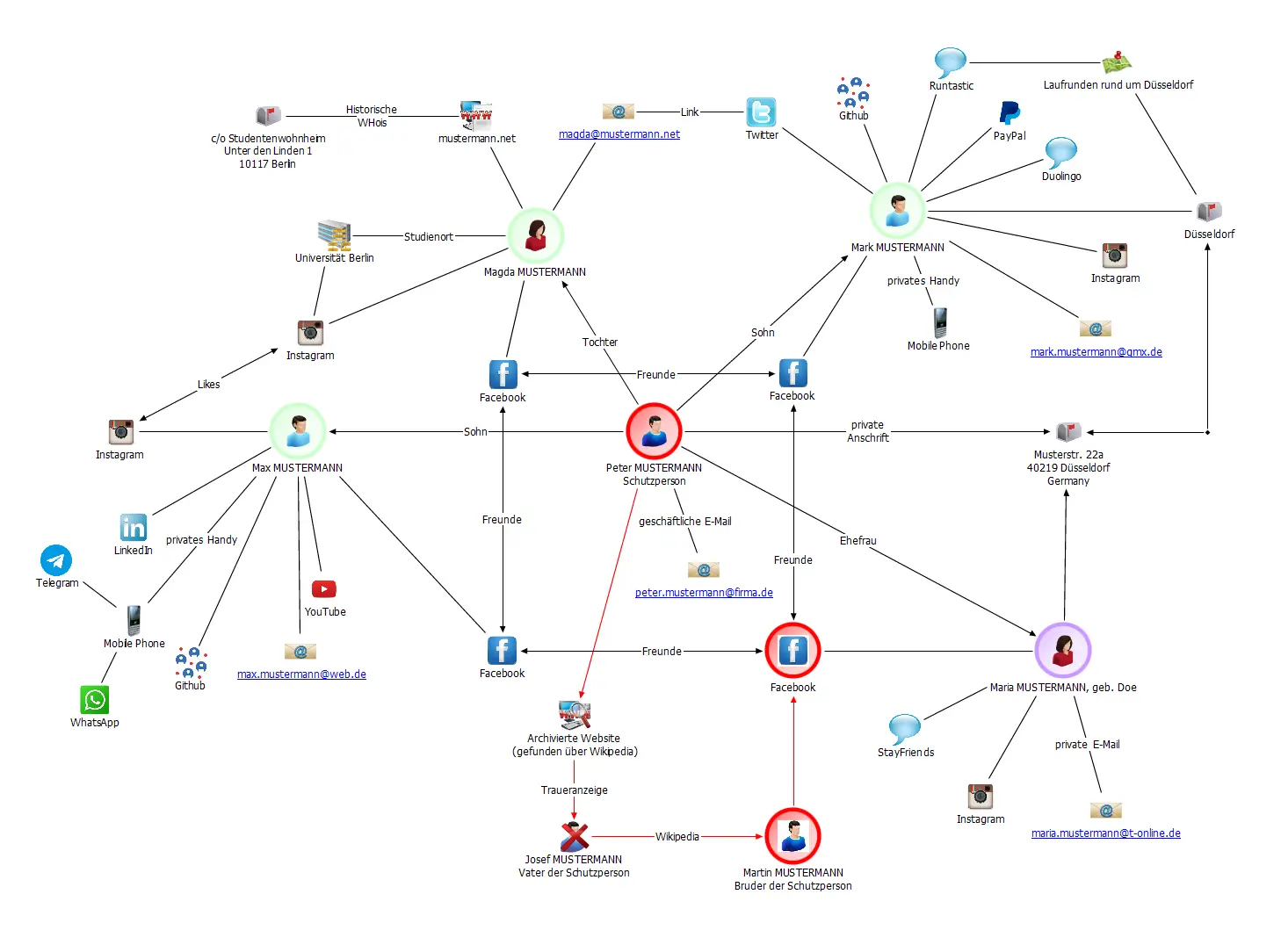
Our digital profile is much more than a reflection of our online activities; it is a complex web of information that we often unknowingly share. In addition to the obvious data such as social media interactions and online transactions, our digital footprint includes more subtle but critical elements. These include leaked login credentials, outdated whois data, online obituaries, and, most explosively, publicly available home addresses and private cell phone numbers. This information, once published in the digital space, can pose a significant risk to personal security.
For executives, VIPs, and other public figures, such information is particularly risky. Not only can it compromise privacy, but it can also lead to real security threats. Therefore, it is critical to be aware of these digital trails and understand how they are created and disseminated. Personal identity information is often collected without our knowledge by data brokers or exposed through data leaks.
A proactive approach is required to effectively control one’s digital footprint. This starts with being aware of your online activities and carefully examining your privacy settings. For those in the public eye, the support of privacy experts such as those at corma GmbH is often essential. They not only offer an analysis of the digital footprint, but also uncover hidden risks and develop effective protection strategies. The goal is to make the digital identity secure and authentic to protect both privacy and personal security.
Various Sources of Personal Information on the Internet
In the digital age, our identity information is widely distributed and often more accessible than we think. Search engines play a central role in this. They index and make discoverable information that we have consciously or unconsciously left online. From contact information on company websites to social media posts, search engines can reveal a wide range of personal information.
But there are even more hidden, potentially dangerous sources: Data leaks. These uncontrolled data flows, often the result of security breaches or data theft, can expose sensitive information such as email addresses, passwords, and even financial data.
Another often-overlooked player in this scenario is the data broker. These companies systematically collect data from a variety of sources and create detailed profiles that they then resell. These profiles and user data can range from innocuous contact information to detailed behavioral and usage patterns.
So where is their data now on the Internet?
The Search Engine as a Potential Threat to Personal Security
Search engines represent a potential risk to personal security because they can act as powerful information retrieval tools. They index and aggregate a wide variety of information from across the Internet, making them a one-stop shop for finding data. Here are some specific reasons why search engines can visualize a security risk:
- Accessibility of personal information: Search engines can make private information such as names, addresses, phone numbers, or email addresses available. This information can be published on various websites, online directories, or social networks. When such information is easily accessible, it can be misused by people with malicious intent.
- Links to sensitive information: Search engines can provide links to sensitive information such as professional profiles, publications, interviews, or articles that may contain private details or opinions. This information can be used to create a comprehensive picture of an individual that could be used for impersonation, stalking, or other forms of harassment.
- Discover connections and networks: When searching for a person, search engines can also reveal connections to family members, coworkers, or other close associates. This information can be used to target or pressure the individual.
- References to past activity: Search engines can also find historical data, such as old blog posts, forum posts, or comments that a person has made in the past. This information can be taken out of context and used against the person without permission.
- Linking to compromised data: In some cases, search engines may also link to data leaks or published compromised data containing sensitive information such as passwords or financial data.
To minimize the risk posed by search engines, it is important to actively manage your online presence. This includes reviewing privacy settings on social networking sites, regularly checking search results for your name, and taking steps to have unwanted information removed. In some cases, the assistance of digital close protection professionals and security experts, such as those offered by companies like corma GmbH, can be critical to ensuring personal safety.
Pro Tip: Targeted Process for Deleting Old and Unwanted Data
When it comes to cleaning up your digital presence, it’s important to go straight to the source. Focus on deleting old and unwanted posts or data directly from the websites or platforms where they were published. Trying to influence Google or other search engines directly can be tedious and often ineffective. Search engines like Google only index existing content on the Internet; they do not remove content from the original websites.
If you remove the original source of an unwanted post or piece of information, it will eventually disappear from search engine results. This may take some time, as search engines must regularly update their indexes, but it is the most effective way to ensure that the information is permanently removed. Keep in mind that on some platforms or websites, removing content may require assistance from the webmaster or customer service. Be persistent and document your requests to expedite the process.
By addressing the sources of your digital footprint head on, you can more effectively regain control of your online presence and improve your digital security.

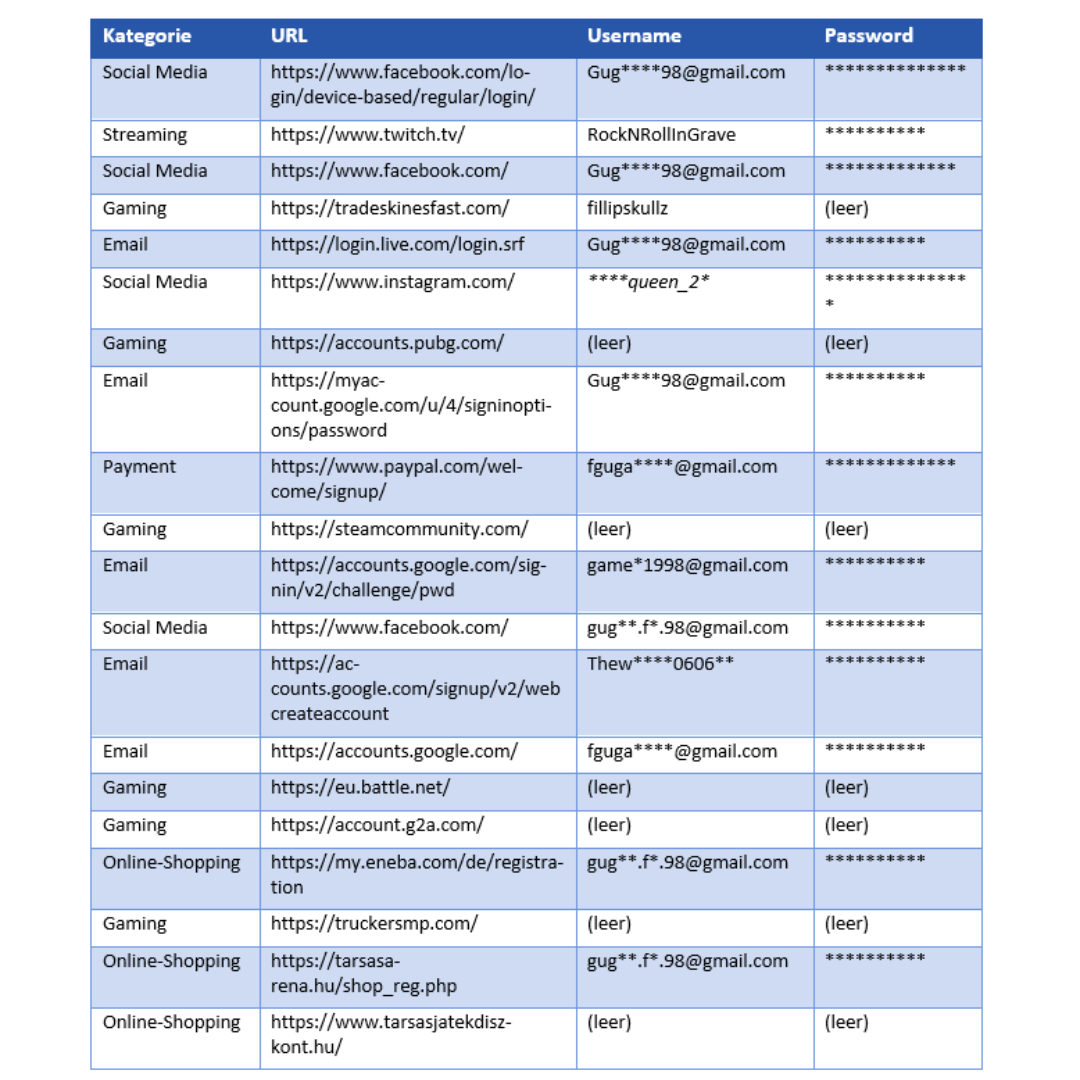
Data Breaches and Infostealers: The Hidden Threat in Cyberspace
Data leaks and data breaches are two sides of the same coin in the world of cybersecurity. While data leaks represent the unintentional loss of data due to security vulnerabilities, data breaches refer to targeted attacks in which hackers actively infiltrate systems to steal sensitive data. This data can include email addresses, passwords, birthdates, financial information, and personal identification numbers. The threat posed by data breaches is enormous, as they not only jeopardize the privacy and security of individuals, but can also severely damage companies and organizations.
Unfortunately, data breaches are a common occurrence. Tools such as the HPI Identity Leak Checker (Hasso Plattner Institute) or “Have I Been Pwned?” by Troy Hunt allow you to check if your data has been compromised. These free services provide an easy way to check your email addresses and other personal information.
Another worrying development is the use of infostealers – malicious programs designed to steal confidential information from infected computers. These programs can gather data, capturing passwords, credit card details and other sensitive information and passing it on to cyber criminals. Users’ stolen information is often offered for sale on the black market or in underground forums on the Internet, putting individuals at increased risk of identity fraud and scams.
In addition, there are online platforms that offer downloadable profiles of individuals compiled from a variety of sources. These profiles (e.g., browser profiles copied from Firefox Mozilla, Chrome, Edge, and other browsers) can contain detailed information about an individual’s personal and professional life and are often sold without their knowledge or consent. For people in public life or with sensitive professional positions, this can lead to serious security concerns. These are millions of records that have been stolen, a truly huge risk!
To protect yourself from the consequences of data breaches and information theft, it is important to maintain a high level of vigilance and security awareness. This includes performing regular security checks, using strong, unique passwords, and being aware of the methods used by cyber criminals. In the event of a suspected hack or data loss, it is advisable to act quickly and seek professional help before your own data is leaked online. Specialized service providers such as corma GmbH can help monitor the spread of information and take effective countermeasures to ensure personal and professional security.
Pro Tip: Strong Passwords: Your First Line of Defense
A strong password is your first line of digital defense. Use a combination of letters, numbers, and special characters, and avoid obvious passwords such as birthdates or simple patterns. Password managers can help you keep track of your different passwords.
Data Brokers: The Invisible Architects of Your Online Identity
In the world of digital close protection, data brokers are an often underestimated but essential component. These companies operate in the background, systematically collecting data from a variety of sources to create detailed profiles of individuals. Platforms such as pipl.com use a unique identity resolution engine that combines personal, professional and social data to create comprehensive profiles. These profiles, which often include direct links to social networks and mobile phone numbers, are created under the guise of fraud prevention and can contain over 3 billion identity profiles.
Other players, such as constella-intelligence and district4lab, use data sets from data breaches over the past 15 years to uncover aliases, nicknames, and domains to build a complete picture of an individual. This information is particularly valuable for investigations because it allows information from multiple sources to be combined and analyzed quickly and efficiently. The databases currently contain over 120 billion records and can be accessed via a website or API interfaces.
Platforms such as FullContact, which specialize in identity resolution and data enrichment, also help companies build a complete picture of their customers. They collect publicly available information from social media, corporate websites, and public databases to enrich customer data and provide a more complete picture of customer interests and preferences.
These comprehensive data collections offered by data brokers can pose a risk to personal security, especially for public figures. Not only do they allow for a profound invasion of privacy, but they can also be misused for unwanted marketing purposes or worse. It is therefore essential for vulnerable people to be aware of the existence and operation of these data brokers and to take appropriate measures to protect their data.
Balancing Transparency and Risk: Private Data in Public Business Registers
Given the easy accessibility of information in our networked world, the presence of private data in corporate registries, business databases and open data sources is proving to be a double-edged sword.
For directors, board members and shareholders, this means that their personal information is often much more open than they might think. Many public registers contain not only business details, but also private information such as home addresses, dates of birth and even ID numbers that have been entered into official documents by notaries. This data is available not only to business partners and investors, but to anyone interested enough to search for it.
While this maximum transparency is encouraged for reasons of accountability and public interest, it carries a high risk. It can lead to unintentional invasions of privacy and make public figures vulnerable to identity theft, fraud and other forms of cybercrime. In addition, this information makes it possible to create networks of connections that allow further inferences to be drawn about personal and professional relationships.
As a result, it is critical for people in vulnerable positions to be aware of the existence and scope of this publicly available data. It is important to regularly review what personal identifying information is available in such databases and to take appropriate measures to protect one’s privacy and security. In some cases, it may be useful to seek professional assistance in monitoring and controlling the dissemination of sensitive data. Experts such as those at corma GmbH can help minimize risk and ensure secure handling of these unavoidable aspects of digital transparency.
Social Media and Online Platforms: Between visibility and safety
The role of social media and online platforms in the dissemination of personal information should not be underestimated. Platforms such as Facebook, Instagram, Twitter and LinkedIn have become central places where people share information about their work, family, hobbies and interests. But these seemingly innocent activities can have unintended consequences. Depending on your privacy settings, this information can be accessible far beyond your circle of friends and acquaintances, opening the door to abuse and identity theft.
Impersonation – pretending to be someone else – is a particular risk on social networks. Often in conjunction with identity theft.
It is not uncommon for profiles to be created on social networks for the purpose of impersonating another person. Such fake profiles can be used for fraudulent purposes or to damage a person’s reputation. There are many instructions on how to do this circulating on the Internet, which are a welcome aid to the attacker.
While social media and online platforms are a great way to network and share information, they also pose personal security risks. It is important to be aware of these risks and take appropriate measures.
Social networks are a hotspot for collecting personal information. Be careful about what information you share on platforms like Twitter and WhatsApp. Regularly review your privacy settings and be aware of what information you make public.
This includes carefully reviewing your privacy settings, being aware of the type of information you share, and regularly checking your own online profile for signs of abuse or impersonation. Public figures may find it useful to seek professional assistance in monitoring and protecting their online presence. Experts such as those at corma GmbH can help manage social media visibility and ensure personal safety.
Digital Traces in Images: The Dissemination of Personal Photographs on the Web
Texts and images alike leave digital traces. When photos of us and our families appear online, they can have far-reaching consequences. Technologies like PimEyes have the capacity to identify people in photos – even in the middle of a group. These highly accurate systems can scour the surface web and understand people in pictures, whether at club meetings or public events.

The availability of such images can have both positive and negative effects. On the one hand, they offer a way to share memories and maintain connections. On the other hand, however, they can also violate privacy and visualize a security risk, especially if they are published without the consent of the people depicted. Images can reveal information about whereabouts, lifestyle and personal relationships that could be misused by third parties.
It is therefore important to be aware of the distribution of your own images on the Internet. Regularly examine where and how your images appear online. Use the privacy settings on social networks and platforms to keep control over who can see your images. In cases where images have been published without your consent, you can take action to have them removed. For public figures, it may also make sense to seek professional support to monitor their digital presence. Services such as corma GmbH offer specialized solutions to monitor the distribution of personal photos on the web and protect privacy and security.
Hidden dangers: Other places personal information can be found online
In addition to the obvious sources such as social media and online platforms, there are other, lesser-known places on the Internet where personal information can be found. One growing risk is data published by ransomware groups. These criminal groups regularly publish content they have stolen in their attacks, especially when victims refuse to pay the ransom. This published data could include your personal information, even if you or your organization were not the direct target of the attack.
Another serious risk is doxing. Doxing is the practice of publishing identifying information about a person on the Internet, such as a person’s real name, home address, place of employment, phone number, financial information, or other personal information. This practice can result in serious privacy violations and security risks.
In addition to these threats, paste bins and chans (forums) are often places where personal information can appear unexpectedly. Bulletin boards are often used to quickly exchange large amounts of data, including sensitive information. Chans are forums where users communicate anonymously and often share or post sensitive information.
Given these multiple risks, it is critical to remain vigilant and regularly review if and where your personal information is appearing online. For public figures or those in sensitive positions, it may be advisable to seek professional help. Experts such as those at corma GmbH can help you monitor the distribution of your information online and take appropriate measures to protect your privacy and security.
Your Data, Your Control: A Conscious Approach to Digital Traces
Now that we’ve highlighted the many ways your personal information can end up online, it’s time to synthesize key insights and motivate proactive action. Our connected world offers endless opportunities, but it also leaves digital trails that pose risks to our privacy and security. The sources from which private information can originate – from search engine results and social media, to data brokers and data exposed by ransomware – are diverse and far-reaching.
The key message of this article is that you should be in control of your data. It’s important to be aware of your digital presence and take proactive steps to protect your information. This includes reviewing privacy settings, regularly monitoring your online presence, and taking steps to remove unwanted information.
We encourage you to become more aware of your personal information. Start by examining your digital footprint and understanding where your information is being published. Use the services of experts such as corma GmbH to conduct a comprehensive analysis of your digital footprint and develop customized protection strategies. Remember, your data is valuable and how it is used is in your hands. Take back control of your digital identity and protect your privacy in the digital age.

Take Control of Your Digital Security – Contact Us Now!
You now have an understanding of the complexity and importance of your digital footprint. Now it’s time to take the next step and actively manage your digital security. At corma GmbH, we are ready to guide you on this journey. Our experts can provide you with personalized advice on how to effectively protect your personal data and secure your digital presence.
Please do not hesitate to contact us. Whether by email, phone or online meeting, we are here to answer your questions and work with you to find the best solutions for your digital security. Simply schedule a consultation through our online calendar: https://corma.de/meeting.
Take advantage of this opportunity to secure your digital identity and protect your privacy. We at corma GmbH look forward to supporting you and working with you to ensure a secure digital future. Contact us now!

