Identity Theft Protection: What information about me can be found online?
“Search for digital evidence”
As identity theft continues to grow in the digital landscape, it’s important to be aware of the risks. Every one of your online activities, every click, contributes to a digital footprint that, if it falls into the wrong hands, can represent a serious threat to your security. This blog post is aimed at a wide audience-from board members and CEOs to VIPs, public figures, and high-net-worth individuals. We all share a common challenge: the need to protect our personal information online.
The digital footprint we leave behind is not only a record of our online activities, but also a potential gateway for identity thieves. Whether it’s simple contact information, professional details, or personal information available online, it can all be misused. In this article, we look at how your personal information online affects your security and the steps you can take to protect yourself from identity theft.
Our goal is not only to make you aware of the risks, but also to show you concrete solutions and strategies that you can use to secure your digital identity. Rely on the expertise of corma GmbH to understand and effectively manage your online presence. Let’s start your digital search for clues together and protect your data online.
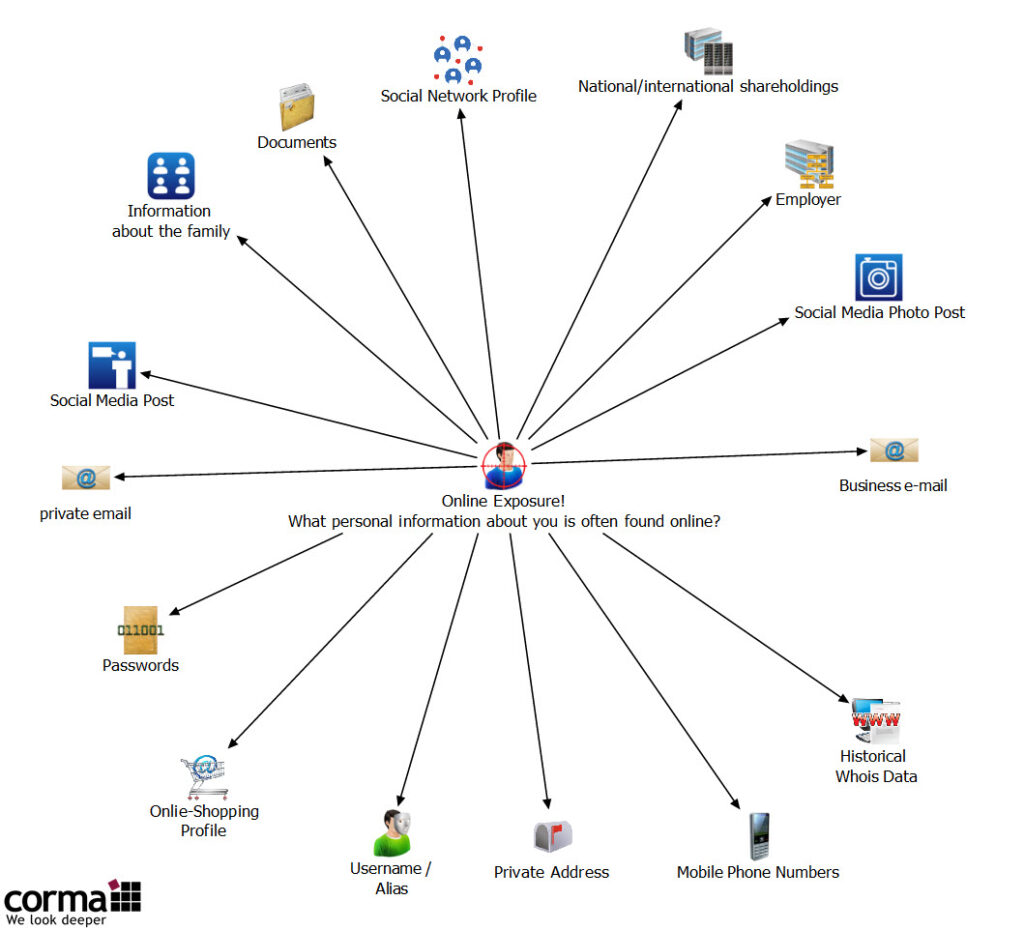
Online exposure: What personal information about you is commonly found online?
Our personal information is often just a click away on the Internet. From home and work addresses to dates of birth, the amount of information available about us on the Internet can be surprising and unsettling. Addresses, for example, are often easy to find and can pose risks such as unwanted contact or even physical security threats. The same is true for birth dates, which, once published, can be used for identity theft.
Contact information, such as cell phone numbers and email addresses, can also be found online. These can be used for unsolicited advertising, fraud, or phishing attacks. Professional information, such as employer or professional email addresses, provides information about our professional careers and networks and can compromise our privacy.
Online identities, such as aliases, are also an important part of our digital footprint. They can create links to our real identities and make us vulnerable to online harassment or reputational damage. Passwords compromised by data leaks pose a significant security risk and can lead to serious data breaches.
The photos and images we share online can reveal a lot about our private lives and are often more accessible than we think. Social media profiles are a goldmine of personal information, often providing detailed insights into our private lives, preferences and habits.
Information such as jogging routes, dog walks, vacation spots and homes, often shared through social media or other online platforms, can reveal a lot about our lifestyles and preferences. This information can be used by cybercriminals to plan targeted attacks or steal our identities.
Similarly, information about our families that is available online can provide sensitive insights into our private lives. Details about family members, their relationships and activities can inadvertently end up online, compromising the privacy of the entire family.
In addition, our interests and hobbies that we share online provide another dimension of personal information. Whether it’s posts on forums, comments on social networking sites, or memberships in online groups, this information can be used by third parties to create a detailed profile of our personality and preferences. This can be used for both personalized marketing and targeted fraud.
In this context, it is important to be aware of the types of information that can be found about us online and to take steps to secure our digital presence. Being aware of how we use our information in the digital space is not only a matter of privacy, but also an important step in protecting our personal security.
From Fragments to Biographies: Reconstructing Your Digital Traces
Piecing together fragmented data is like putting together a jigsaw puzzle, with each piece providing a more complete picture of your online identity. Whether it’s an old email address, a forgotten online forum membership, or a long-abandoned phone number, each piece can provide important clues. Digital forensics and identity protection experts use specialized analysis techniques to build a complete profile from this scattered information. These profiles are critical not only for identifying and understanding a person’s online presence, but also for assessing potential risks and threats.

A classic example is reconstructing an executive’s digital history. By combining current and outdated data, new insights can be gained, such as connections to previous employers or hidden online activity. This information is particularly valuable for understanding risks such as identity theft or targeted cyberattacks and taking preventative measures.
It is therefore essential for public figures and those in sensitive positions to develop a deep understanding of their digital footprint. The support of experts who are able to piece together the scattered data into a coherent picture is a crucial step in this process. At corma GmbH, we provide this expertise to ensure your digital security and protect you from the risks associated with the uncontrolled dissemination of personal data. Our goal is not only to provide you with insight into your digital presence, but also to offer you practical solutions for the secure handling of your personal data online.
The Dark Side of the Digital Age: Identity Theft and Its Consequences
In the age of digitalization, identity theft is an increasingly worrisome threat. Cybercriminals use personal information such as your name, address, or credit card details to commit fraud in your name. The consequences can range from financial loss to serious threats to your credit and identity. Especially dangerous are leaked email addresses and passwords, which cybercriminals use as a gateway for phishing attacks and fraud. These criminals use sophisticated methods, such as spoofed emails or Web sites, to gain access to your sensitive information, which can lead not only to identity theft but also to reputational damage.
For public figures such as executives or VIPs, it is essential to carefully monitor their digital presence and take proactive measures to protect their data. Working with specialized service providers like corma GmbH can be critical to understanding and defending against digital threats. It is important to be aware of the risks and take steps such as reviewing privacy settings, using strong passwords and regularly monitoring online accounts. In addition, you should respond immediately to any suspicious activity, such as reporting it to the police or contacting Schufa and other credit reporting agencies.
In this blog post, you will learn how to effectively protect yourself from identity theft and other online threats to maintain your personal and professional integrity in the digital world. We’ll show you how to protect your digital identity and stay safe from the shadows of the digital age.
Active security measures: Effectively protect your digital identity
With identity theft and cybercrime on the rise, it is increasingly important to actively protect your digital identity. Start by regularly reviewing and adjusting your privacy settings. This is especially important on social networking sites and when using various online services. Ensure that your personal information is not unnecessarily exposed to the public to minimize the risk of identity theft and data misuse.
Another important step is to use strong, unique passwords for all your online accounts. Consider using two-factor authentication to further secure your accounts. Be careful about the information you share online, especially on platforms like Facebook or Instagram. Even small details can be used by cybercriminals to compromise your identity or commit fraud in your name.
Professional privacy services, such as those offered by experts like corma GmbH, play a critical role in protecting your digital identity. These experts not only provide a comprehensive analysis of your digital footprint, but also develop customized solutions to protect your data from unauthorized access and misuse. They can help you identify risks early and take effective countermeasures.
In an age where digital threats are everywhere, being proactive is essential. Manage your online presence carefully and enlist the help of privacy experts to protect your personal information and digital identity. With the right strategies and tools, you can protect yourself from identity theft and other online threats.
Protect your digital life
Start protecting your digital identity today with Corma’s expert solutions. From privacy settings to two-factor authentication, we offer the all-around protection you need. Let’s work together to strengthen your digital security.
Conclusion: Awareness is the key to protecting personal data
The results of our identity theft research are clear and unequivocal: being aware of your personal information is essential to staying safe in the digital world. Identity theft is a real and common threat that can affect everyone from executives to consumers. The risks range from fake transactions to fraudulent activities in your name. That is why it is critical to carefully manage and protect your digital footprint.
Reviewing and adjusting your privacy settings, using strong and unique passwords, and regularly monitoring your online accounts are basic steps to protect yourself from identity theft. It is also advisable to use professional data protection services that specialize in protecting against identity theft and other online threats. Companies like corma GmbH offer customized solutions to secure your digital identity and protect your sensitive information from misuse.
We encourage you to take action and manage your digital presence carefully. Be wary of phishing emails, consider the authenticity of senders, and be careful when sharing sensitive information. Remember, taking a proactive approach to your personal information is the best way to protect yourself from the many risks of the digital age. Take your digital security seriously and take the necessary steps to protect your identity and information.
Your Identity Theft Protection Starts Here
Are you concerned about your digital security? Want to learn more about how to effectively protect yourself and your personal information online? Please do not hesitate to contact us. We at corma GmbH are ready to support you with our expertise.
Simply contact us for a consultation. Whether by email, phone or online meeting, we are here to discuss your individual needs and develop customized solutions for your digital protection.
Visit corma.de/meeting to schedule your free personal consultation. Together, we can make sure your digital identity stays safe. Take the first step towards total digital security now!
FAQ – Frequently Asked Questions: Deleting personal information from the Internet
What is the right to have data deleted?
The right to erasure, also known as the “right to be forgotten,” is an essential part of data protection, especially in the context of the European General Data Protection Regulation (GDPR). It allows individuals to request the deletion of their personal data, provided certain conditions are met. These include situations where the data is no longer needed for the original purpose for which it was collected, or where the data subject withdraws their consent to data processing.
The right to erasure applies not only to the removal of data from search engines such as Google, but also to websites, databases and archives. It includes the deletion of outdated, misleading, incomplete or unlawfully processed data. This right is particularly relevant to online privacy, as it allows individuals to control their online presence and the dissemination of their personal information.
However, it is important to note that the right to erasure is not absolute. It must be balanced against the public interest and the rights of others, such as freedom of expression. In certain cases, for example, where data processing is necessary for the exercise of the right to freedom of expression and information, or for reasons of public interest in the area of public health, the right to erasure may be limited.
In summary, the right to erasure enables individuals to regain control over their personal data in the digital space and helps to protect their privacy and digital identity.
When can you exercise your right to data removal?
The right to erasure, also known as the “right to be forgotten,” can be exercised in a variety of situations. Here are some of the most common:
No longer necessary: If personal information is no longer necessary for the purposes for which it was originally collected or processed, erasure may be requested.
Withdrawal of consent: If the processing of the data is based on the consent of the data subject and the data subject withdraws his or her consent without any other legal basis for the processing.
Unlawful processing: When the data is processed unlawfully, for example, without complying with data protection regulations.
Objection to processing: When the data subject objects to the processing of his or her data and there are no overriding legitimate grounds for the processing.
Legal requirements: Where erasure is necessary to comply with a legal obligation to which the controller is subject.
Children’s data: In particular, when collecting data from children in connection with the use of Internet services.
It is important to note that the right to erasure is not absolute and may be subject to restrictions in certain cases, such as where processing is necessary for the exercise of the right of expression and information, for compliance with a legal obligation, or for reasons of public interest in the area of public health.
What steps are required to request data deletion?
Deleting data, especially online, can be a complex process depending on the type of data and platform. Here are the basic steps to follow:
Identify the data: First, you need to determine exactly what data you want to delete. This could be personal information on a social media platform, in an online forum, or in the search results of a search engine.
Contact the data controller: Contact the website, service, or platform where your information is stored. Many companies have dedicated privacy officers or contact forms for such requests.
Formal request: Submit a formal request for data deletion. This request should clearly and precisely state what data should be deleted and why. It is helpful to refer to the specific data protection laws or guidelines that apply in your country or region, such as the GDPR in the European Union.
Proof of lawfulness: You may need to prove that the data was collected unlawfully, is no longer relevant, or violates your rights. In some cases, it may be necessary to confirm your identity to prevent misuse.
Waiting for a response: After submitting your request, you will need to wait for a response. Processing time may vary depending on the company and its policies.
Follow-up requests: If your request is denied or there is no response, you can make a follow-up request or contact a supervisory authority. In some countries, there are special data protection authorities that can help in such cases.
Review: After the data has been deleted, it is a good idea to review it. In some cases, it may take some time for the data to be completely removed from all systems.
It is important to note that not all data removal requests are approved. In some cases, companies or platforms may have legitimate reasons to retain certain data, such as for legal or security reasons.
How do I remove outdated information from search engines?
There are several steps you can take to get outdated information removed from search engines like Google. First, you should try to contact the owner of the website where the outdated information is posted and request that the content be removed. Once the content has been removed from the site, you can use Google’s “Update outdated content” tool to request that the search results be updated.
If the content violates Google policies or contains personal information, you can submit a removal request. Google provides different forms for different types of requests, such as removing offensive or intimate personal images, unauthorized pornography, or personal information.
You can find the appropriate forms on the “Removing information from Google” help page.
What is the legal basis for the right of erasure?
The right to erasure, also known as the “right to be forgotten,” is enshrined in the European Union’s General Data Protection Regulation (GDPR). This right allows individuals to request the erasure of their personal data, provided that certain conditions are met.
The legal grounds for the right to erasure include:
Compliance with a legal obligation: under Article 17 of the GDPR, individuals have the right to request the erasure of their data if the processing is no longer lawful, for example, if the data processing is in breach of the GDPR.
Data that is no longer needed: If personal data is no longer necessary for the purposes for which it was originally collected or processed, erasure can be requested.
Withdrawal of consent: If the processing of the data is based on the consent of the data subject, and the data subject withdraws his or her consent without any other legal basis for the processing.
Objection to Processing: Individuals have the right to object at any time to the processing of their personal data on grounds relating to their particular situation.
Unlawful processing: Where the processing of personal data has been carried out unlawfully, for example, without the necessary consent or in breach of the GDPR.
Legal requirements: Erasure may be necessary to comply with a legal obligation imposed on the data controller under European Union or Member State law.
However, the right to erasure is not absolute and may be subject to restrictions, for example where the processing is necessary for the exercise of the right of freedom of expression and information, for compliance with a legal obligation, for reasons of public interest, or for the establishment, exercise or defense of legal claims.
What types of personal information can be deleted?
You can have several types of personal information on the Internet deleted, especially if it is outdated, misleading, or has been processed unlawfully.
This includes:
First and last name: If your full name appears online in a way that compromises your privacy or security, you can request that it be removed.
Addresses: Home and business addresses can be removed from online directories or other websites, especially if they present a security risk.
Contact Information: This includes phone numbers and email addresses that have been published without your consent.
Pictures and videos: Photos or videos that show you in person and have been posted online without your consent can be requested for removal.
Professional information: Information about your work history that is outdated or incorrect can also be removed.
Social media content: Posts or comments on social networking sites that could damage your reputation can also be deleted.
Personal information in databases: Entries in online databases or search engines that contain personal information may be deleted.
It is important to note that the right to erasure of personal data is strengthened by the General Data Protection Regulation (GDPR) in the EU and similar laws in other countries. However, the data erasure process may vary depending on the platform and the type of data.

